Builder is the first medium-difficulty HTB machine I have completed – the lower difficulty machines were a bit too easy for me and too straightforward. I wanted to feel the same frustrations of the learning process when I took my SANS courses, spinning my wheels and running into dead ends until I finally figured it out – and Builder delivered!
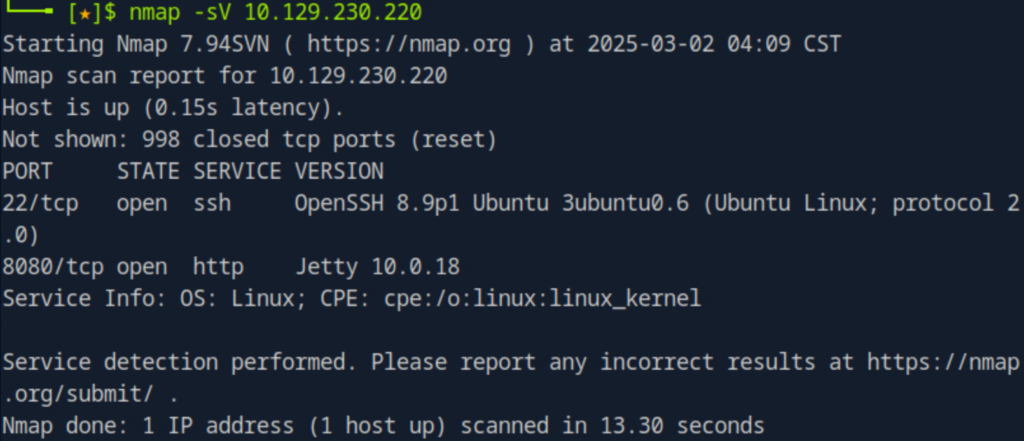
As typical HTB machines, I was provided with an IP address and nothing else. First order of business – recon! Nmap reveals two running services:
- OpenSSH – which means I will likely have some sort of SSH interaction
- Jetty – a Java web server, indicating some sort of web component will be involved
Sure enough, opening the IP in a browser reveals a Jenkins dashboard. Jenkins is a Java-based automation tool for developing software, an area I have little knowledge of. But I know any type of automation or orchestration tool is an opportunity, so this might be worth an explore.
Since we have app names and version numbers for OpenSSH, Jetty, and Jenkins, I search for known vulnerabilities with $favoriteSearchEngine and find the following:
- OpenSSH 8.9p1 – there is a known vuln that allows RCE
- Jetty 10.0.18 – there’s a DoS vuln and an insufficient validation vuln that could lead to a open redirect attack or a SSRF
- Jenkins 2.441 – there’s a juicy file read vuln that allows RCE
Multiple avenues of attack here, but Jenkins is something I have never worked with, so I decide to get nosy in the web UI. I quickly find you can’t do much as an unauthenticated user, but see one of the usernames is jennifer. Additionally, a quick check of Jenkins docs shows the default admin account is ‘admin’. I try some quick common admin/pw combinations before using Burp to dictionary attack the jennifer account. Bam, password revealed.
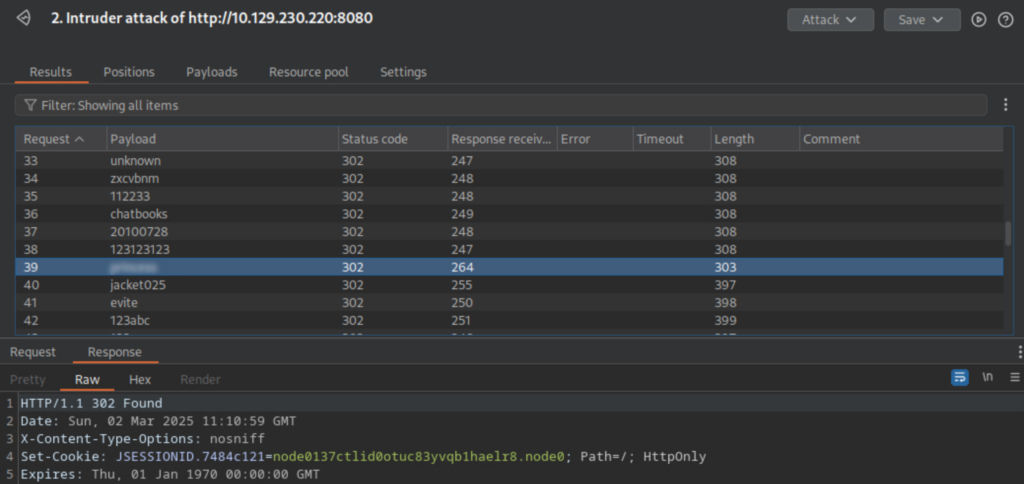
With Jennifer’s account creds, I log into Jenkins and start digging around. I run into two interesting things – the ability to run Windows and bash commands via jobs, and access to add and review keys. There is one key stored for root, so I decide to concentrate on that first. Rooting around (ha), a something jumps out at me: “Concealed for Confidentiality”, keyword “concealed“. This can’t be what I’m thinking….can it?
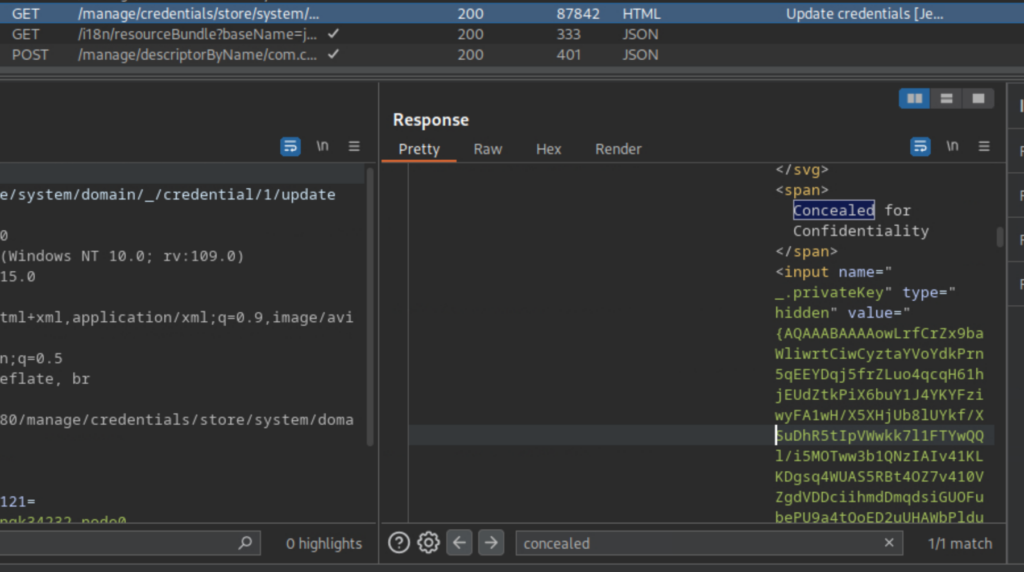
It is, kind of. It’s encrypted. However… a quick web search for “Jenkins credentials decrypt” brought me to a 7 year old StackExchange post that shows me how to use Jenkins’ built-in script engine to decode the encrypted text and extract the key. Incredible.
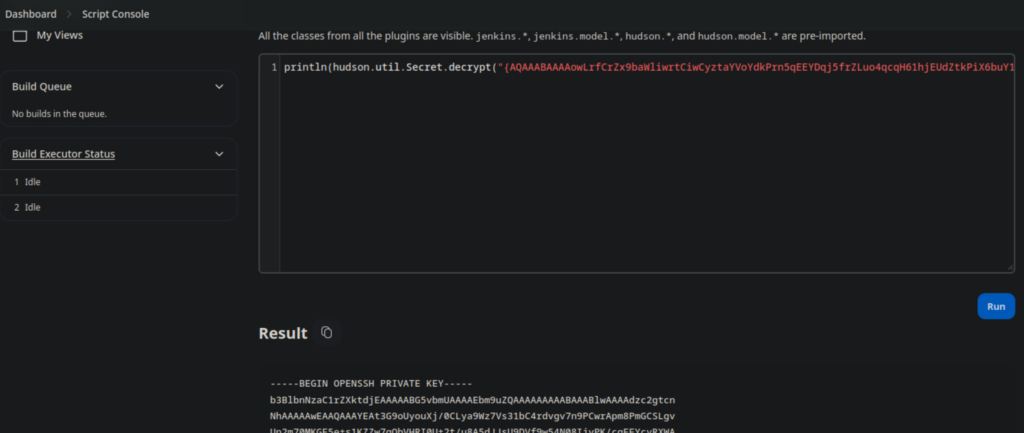
With the ssh private key for root in my possession, I install it onto my machine and initiate an ssh into the target box…
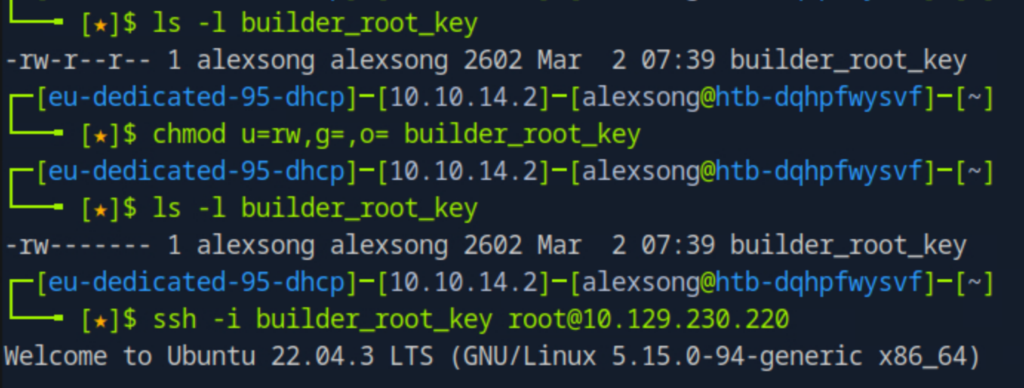
I’m in.
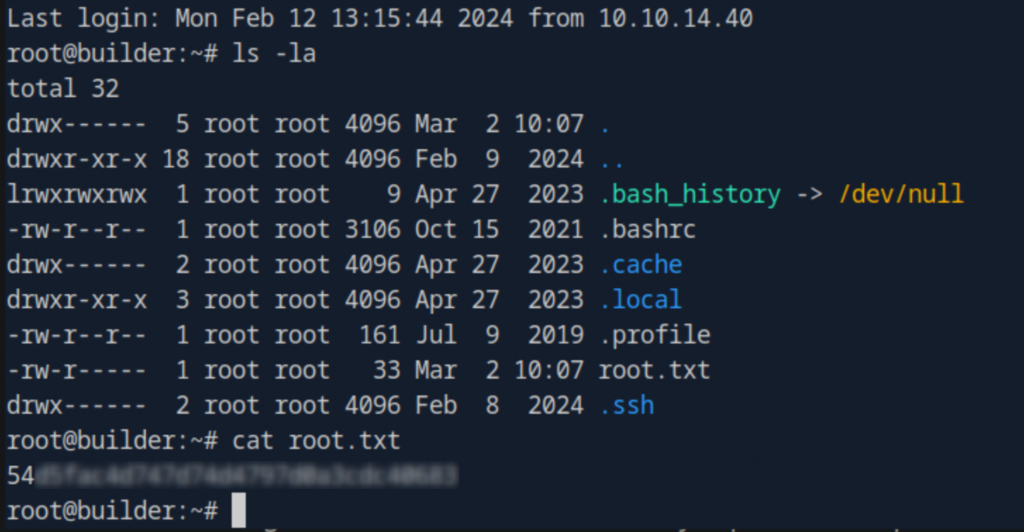
Fortunately, there are no additional twists. The root flag is right there, win!


Leave a Reply